Microsoft has identified Nigerian developer Joshua Ogundipe as the alleged architect behind RaccoonO365, the fastest-expanding phishing campaign targeting Microsoft 365 users globally. The company’s Digital Crimes Unit (DCU) announced the takedown of 338 websites linked to this operation, effectively dismantling the criminal infrastructure responsible for harvesting thousands of login credentials across 94 countries.
Known internally as Storm-2246, RaccoonO365 operates as a phishing-as-a-service platform, enabling even those with minimal technical expertise to mimic Microsoft login portals and capture usernames and passwords with ease.
Since its emergence in July 2024, this service has compromised at least 5,000 Microsoft accounts, with attacks focusing on highly sensitive sectors such as healthcare. One notable campaign targeted over 2,300 organizations in the United States with tax-themed phishing emails, including more than 20 hospitals and medical providers. Microsoft warns these breaches could disrupt patient care, distort laboratory results, and pave the way for ransomware infections.
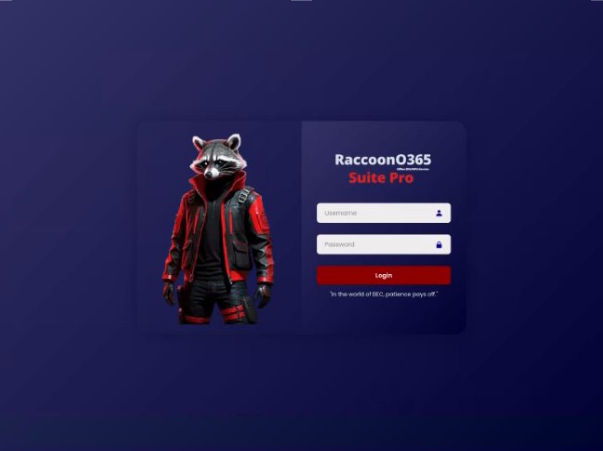
“This investigation highlights that cybercriminals don’t need advanced skills to inflict widespread damage,” stated Microsoft’s DCU. “Tools like RaccoonO365 democratize cybercrime, putting millions of users at significant risk.”
Revealing Joshua Ogundipe
Microsoft’s probe traced the phishing operation back to Joshua Ogundipe, a developer based in Nigeria believed to have authored much of the RaccoonO365 codebase. Ogundipe and his associates reportedly marketed phishing subscriptions on Telegram to a community exceeding 850 members, collecting at least $100,000 in cryptocurrency payments-though Microsoft suspects the actual revenue is considerably higher.
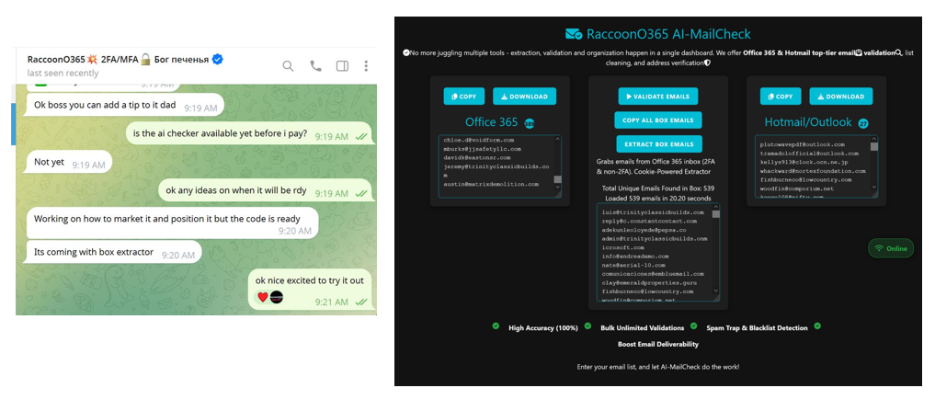
Subscribers gained the capability to launch thousands of phishing attacks daily, amounting to hundreds of millions of fraudulent messages annually. The group also distributed AI-powered tools such as RaccoonO365 AI-MailCheck, designed to evade email filters and increase the success rate of their scams.
Microsoft describes Ogundipe’s operation as resembling a startup, complete with software development, marketing efforts, and customer support for fellow cybercriminals. To obscure their identities, they registered domains using fictitious names and addresses. A critical breakthrough occurred when the group inadvertently compromised a cryptocurrency wallet, enabling investigators to link their online activities to real-world identities.
An international criminal referral has been submitted to law enforcement agencies worldwide, paving the way for legal action against Ogundipe and his network.
Microsoft’s coordinated global crackdown
The shutdown of 338 domains represents just one facet of Microsoft’s comprehensive approach to dismantling phishing infrastructures and sending a clear message to cybercriminals everywhere. Collaborating with Cloudflare, Microsoft disabled malicious websites and employed blockchain analysis tools like Chainalysis Reactor to trace illicit payments and build a robust case.
Despite these efforts, Microsoft cautions that cybercriminals often attempt to rebuild their networks after takedowns. The company remains vigilant, continuously monitoring for new RaccoonO365-related infrastructure and prepared to take further legal measures as needed.
“This operation exemplifies the power of collaboration between technology firms, cybersecurity experts, and governments,” Microsoft emphasized. “By disrupting criminal networks, we cut off their revenue and safeguard millions of users worldwide.”
Related: Microsoft to retire Skype in May 2025, encourages transition to Teams
RaccoonO365 illustrates how cybercrime has evolved into a scalable, global enterprise. Instead of requiring advanced hacking skills, aspiring criminals can purchase phishing kits as a service and launch mass attacks with minimal effort.
This case underscores the critical importance of robust security measures. Microsoft urges individuals and organizations to activate multi-factor authentication (MFA), maintain up-to-date software, and educate employees on recognizing phishing attempts-key steps to prevent stolen credentials from escalating into major security breaches.

Microsoft’s decisive action against RaccoonO365 marks its most forceful campaign yet to combat phishing threats. For Nigeria, this case highlights the presence of cybercrime syndicates within its borders and the necessity for international cooperation to bring offenders to justice. With Ogundipe publicly named, the future of RaccoonO365-and the vast phishing campaigns it enabled-remains uncertain.
















0 Comments